 CCNA考试题库之二:最新640802v
CCNA考试题库之二:最新640802v


《CCNA考试题库之二:最新640802v》由会员分享,可在线阅读,更多相关《CCNA考试题库之二:最新640802v(45页珍藏版)》请在装配图网上搜索。
1、101. Which of the following are true regarding the command output shown in the display? (Choose two.)A. There are at least two routers participating in the RIP process.B. A ping to 192.168.168.2 will be successful.C. A ping to .2 will be successful.D. RtrA has three interfaces participating in the R
2、IP process.Answer: AC102. What three pieces of information can be used in an extended access list to filter traffic? (Choose three.)A. protocolB. VLAN numberC. TCP or UDP port numbersD. source switch port numberE. source IP address and destination IP addressF. source MAC address and destination MAC
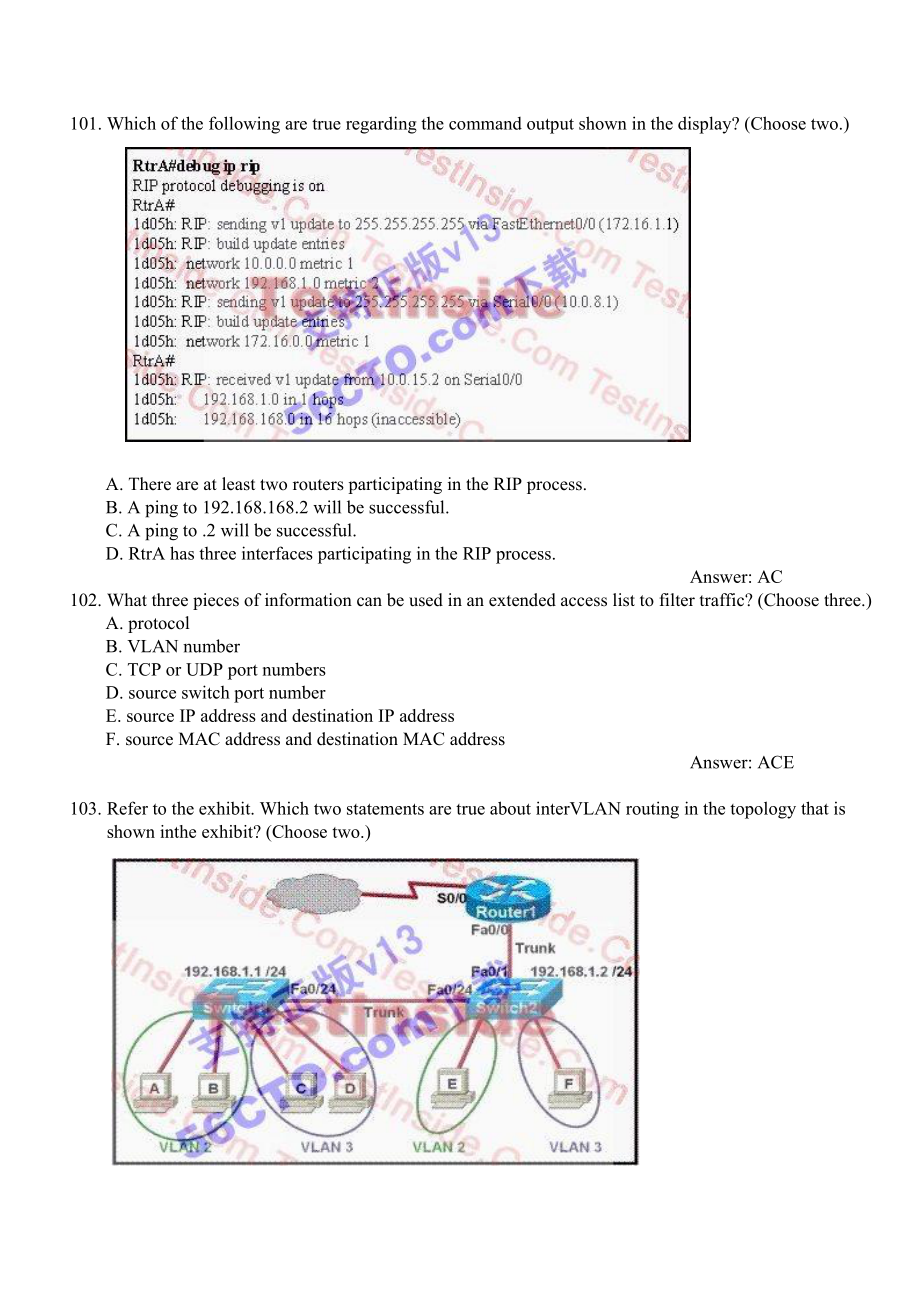
3、addressAnswer: ACE103. Refer to the exhibit. Which two statements are true about interVLAN routing in the topology that is shown inthe exhibit? (Choose two.)A. Host E and host F use the same IP gateway address. B. Router1 and Switch2 should be connected via a crossover cable.C. Router1 will not play
4、 a role in communications between host A and host D. D. The FastEthernet 0/0 interface on Router1 must be configured with subinterfaces.E. Router1 needs more LAN interfaces to accommodate the VLANs that are shown in the exhibit. F. The FastEthernet 0/0 interface on Router1 and Switch2 trunk ports mu
5、st be configured using the same encapsulation type.Answer: DF104. What is the effect of using the service password-encryption command? A. Only the enable password will be encrypted.B. Only the enable secret password will be encrypted.C. Only passwords configured after the command has been entered wi
6、ll be encrypted.D. It will encrypt the secret password and remove the enable secret password from the configuration.E. It will encrypt all current and future passwords.Answer: E105. Refer to the exhibit. For what two reasons has the router loaded its IOS image from the location that is shown? (Choos
7、e two.)A. Router1 has specific boot system commands that instruct it to load IOS from a TFTP server.B. Router1 is acting as a TFTP server for other routers. C. Router1 cannot locate a valid IOS image in flash memory.D. Router1 defaulted to ROMMON mode and loaded the IOS image from a TFTP server.E. C
8、isco routers will first attempt to load an image from TFTP for management purposes.Answer: AC106. At which OSI layer is a logical path created between two host systems? A. sessionB. transportC. networkD. data link E. physical Answer: C107. What functions do routers perform in a network? (Choose two.
9、) A. packet switchingB. access layer securityC. path selection D. VLAN membership assignmentE. bridging between LAN segmentsF. microsegmentation of broadcast domainsAnswer: AC108. Refer to the exhibit. The show vtp status command is executed at a switch that is generating the exhibited output. Which
10、 statement is true for this switch?A. The switch forwards its VLAN database to other switches in the ICND VTP domain.B. The configuration revision number increments each time the VLAN database is updated.C. The switch forwards VTP updates that are sent by other switches in the ICND domain. D. The VL
11、AN database is updated when VTP information is received from other switches.Answer: C109. A Cisco router is booting and has just completed the POST process. It is now ready to find and load an IOS image. What function does the router perform next?A. It checks the configuration register.B. It attempt
12、s to boot from a TFTP server.C. It loads the first image file in flash memory.D. It inspects the configuration file in NVRAM for boot instructions. Answer: A110. Refer to the exhibit. The output that is shown is generated at a switch. Which three of these statements are true? (Choose three.)A. All p
13、orts will be in a state of discarding, learning, or forwarding.B. Thirty VLANs have been configured on this switch. C. The bridge priority is lower than the default value for spanning tree. D. All interfaces that are shown are on shared media.E. All designated ports are in a forwarding state.F. This
14、 switch must be the root bridge for all VLANs on this switch.Answer: ACE111. What is the function of the command switchport trunk native vlan 999 on a Cisco Catalyst switch?A. It creates a VLAN 999 interface.B. It designates VLAN 999 for untagged traffic.C. It blocks VLAN 999 traffic from passing on
15、 the trunk.D. It designates VLAN 999 as the default for all unknown tagged traffic.Answer: B112. Refer to the exhibit. After a RIP route is marked invalid on Router_1, how much time will elapse before that route is removed from the routing table?A. 30 seconds B. 60 seconds C. 90 seconds D. 180 secon
16、ds E. 240 secondsAnswer: B113. When a new trunk is configured on a 2950 switch, which VLANs by default are allowed over the trunk link?A. no VLANs B. all VLANsC. only VLANs 1 - 64D. only the VLANs that are specified when creating the trunkAnswer: B114. Which three statements describe the differences
17、 between RIP version 1 and RIP version 2? (Choose three.)A. RIP version 1 broadcasts updates whereas RIP version 2 uses multicasts.B. RIP version 1 multicasts updates while RIP version 2 uses broadcasts.C. Both RIP version 1 and RIP version 2 are classless routing protocols. D. RIP Version 2 is a cl
18、assless routing protocol whereas RIP version 1 is a classful routing protocol.E. Both RIP version 1 and version 2 support authentication.F. RIP version 2 sends the subnet mask in updates and RIP version 1 does not.Answer: ADF 115. An access list was written with the four statements shown in the grap
19、hic. Which single access list statement will combine all four of these statements into a single statement that will have exactly the same effect?A. access-list 10 permit 172.29.16.0 .255B. access-list 10 permit 172.29.16.0 .255C. access-list 10 permit 172.29.16.0 .255D. access-list 10 permit 172.29.
20、16.0 .255Answer: C116. Refer to the exhibit. All of the routers in the network are configured with the ip subnet-zero command. Which network addresses should be used for Link A and Network A? (Choose two.)Answer: BD117. At which layers of the OSI model do WANs operate? (Choose two.)A. application la
21、yerB. session layerC. transport layerD. network layerE. datalink layerF. physical layerAnswer: EF118. Refer to the exhibit. A network associate has configured the internetwork that is shown in the exhibit, but has failed to configure routing properly. Which configuration will allow the hosts on the
22、BranchLAN to access resources on the HQ LAN with the least impact on router processing and WANbandwidth?A.B.HQ(config)# router ripHQ(config-router)# network 192.168.2.0 HQ(config-router)# network 172.16.0.0 Branch(config)# router ripC.HQ(config)# router eigrp 56HQ(config-router)# network 192.168.2.4
23、 Branch(config)# router eigrp 56D. HQ(config)# router ospf 1HQ(config-router)# network 192.168.2.4 .3 area 0 HQ(config-router)# network 172.16.25.0 .255 area 0Branch(config)# router ospf 1Branch (config-router)# network 192.168.1.0 .255 area 0Branch (config-router)# network 192.168.2.4 .3 area 0Answ
24、er: A119. Refer to the exhibit. What is the purpose of the configuration that is shown?A. to translate addresses of hosts on the fa0/0 and fa0/1 networks to a single public IP address for Internet access B. to translate the internal address of each host on fa0/0 and fa0/1 to a unique external IP add
25、ress for Internet accesC. to provide security on fa0/0 and fa0/1 through the application of an access listD. to allow IP hosts on the Internet to initiate TCP/IP connections to hosts on fa0/0 and fa0/1Answer: A120. A network administrator wants to ensure that only the server can connect to port Fa0/
26、1 on a Catalyst switch.The server is plugged into the switch Fa0/1 port and the network administrator is about to bring the server online. What can the administrator do to ensure that only the MAC address of the server is allowed by switch port Fa0/1? (Choose two.)A. Configure port Fa0/1 to accept c
27、onnections only from the static IP address of the server.B. Employ a proprietary connector type on Fa0/1 that is incompatible with other host connectors. C. Configure the MAC address of the server as a static entry associated with port Fa0/1.D. Bind the IP address of the server to its MAC address on
28、 the switch to prevent other hosts from spoofing the server IP address.E. Configure port security on Fa0/1 to reject traffic with a source MAC address other than that of the server.F. Configure an access list on the switch to deny server traffic from entering any port other than Fa0/1.Answer: CE121.
29、 The OSPF Hello protocol performs which of the following tasks? (Choose two.)A. It provides dynamic neighbor discovery.B. It detects unreachable neighbors in 90 second intervals.C. It maintains neighbor relationships.D. It negotiates correctness parameters between neighboring interfaces.E. It uses t
30、imers to elect the router with the fastest links as the designated router.F. It broadcasts hello packets throughout the internetwork to discover all routers that are running OSPF.Answer: AC122. Which two passwords must be supplied in order to connect by Telnet to a properly secured Cisco switch and
31、make changes to the device configuration? (Choose two.)A. console passwordB. vty password C. aux passwordD. tty passwordE. enable secret passwordF. username passwordAnswer: BE123. Refer to the exhibit. What IP address should be assigned to Workstation A? Answer: C124. Refer to the exhibit. Which add
32、ress and mask combination represents a summary of the routes learned by EIGRP? A. 192.168.25.0 255.255.255.240 B. 192.168.25.0 255.255.255.252 Answer: C125. An inbound access list has been configured on a serial interface to deny packet entry for TCP and UDP ports 21, 23 and 25. What types of packet
33、s will be permitted by this ACL? (Choose three.)A. FTPB. TelnetC. SMTPD. DNSE. HTTPF. POP3Answer: DEF126. Users on the 172.17.22.0 network cannot reach the server located on the 172.31.5.0 network. The network administrator connected to router Coffee via the console port, issued the show ip route co
34、mmand, and was able to ping the server. Based on the output of the show ip route command andthe topology shown in the graphic, what is the cause of the failure?A. The network has not fully converged.B. IP routing is not enabled. C. A static route is configured incorrectly. D. The FastEthernet interf
35、ace on Coffee is disabled.E. The neighbor relationship table is not correctly updated. F. The routing table on Coffee has not updated .Answer: C127. Why does the data communication industry use the layered OSI reference model? (Choose two.)A. It divides the network communication process into smaller
36、 and simpler components, thus aiding component development, design, and troubleshootingB. It enables equipment from different vendors to use the same electronic components, thus saving research and development funds.C. It supports the evolution of multiple competing standards, and thus provides busi
37、ness opportunities for equipment manufacturers.D. It encourages industry standardization by defining what functions occur at each layer of the model.E. It provides a means by which changes in functionality in one layer require changes in other layers.Answer: AD 128. Refer to the exhibit. RIPv2 is in
38、 use on the network with no standard policy in place for summarization. A packet arrives at CentralRouter with a destination IP address of 208.149.23.91. Given the output that is shown,how will CentralRouter process that packet?A. It will forward the packet to 190.171.23.10.B. It will forward the pa
39、cket to 190.171.23.12.C. It will forward the packet to 192.168.33.1.D. It will hold the packet for 22 seconds.E. It will hold the packet for 21 seconds.F. It will discard the packet because there is no matching route.Answer: B129. The network security policy requires that only one host be permitted
40、to attach dynamically to each switchinterface. If that policy is violated, the interface should shut down. Which two commands must the networkadministrator configure on the 2950 Catalyst switch to meet this policy? (Choose two.)A. Switch1(config-if)# switchport port-security maximum 1B. Switch1(conf
41、ig)# mac-address-table secureC. Switch1(config)# access-list 10 permit ip hostD. Switch1(config-if)# switchport port-security violation shutdown E. Switch1(config-if)# ip access-group 10 Answer: AD 130. Refer to the exhibit. A network associate has configured OSPF with the command:City(config-router
42、)# network 192.168.12.64 .63 area 0After completing the configuration, the associate discovers that not all the interfaces are participating in OSPF.Which three of the interfaces shown in the exhibit will participate in OSPF according to this configurationstatement? (Choose three.)A. FastEthernet0 /
43、0 B. FastEthernet0 /1C. Serial0/0D. Serial0/1.102 E. Serial0/1.103F. Serial0/1.104 Answer: BCD 131. Refer to the exhibit. Explain how the routes in the table are being affected by the status change on Interface Ethernet0.A. The router is requesting updates for these networks from routers that are co
44、nnected to interface Ethernet1.B. The router is poisoning the routes and broadcasting the new path costs via interface Ethernet1. C. The router is receiving updates about unreachable networks from routers that are connected to interface Ethernet1.D. The router is poisoning the routes and multicastin
45、g the new path costs via interface Ethernet1. Answer: D132. Which statement is correct about the internetwork shown in the diagram?A. Switch 2 is the root bridge.B. Spanning Tree is not running.C. Host D and Server 1 are in the same network.D. No collisions can occur in traffic between Host B and Ho
46、st C.E. If Fa0/0 is down on Router 1, Host A cannot access Server 1.F. If Fa0/1 is down on Switch 3, Host C cannot access Server 2.Answer: E133. Which statements are true about EIGRP successor routes? (Choose two.)A. A successor route is used by EIGRP to forward traffic to a destination.B. Successor
47、 routes are saved in the topology table to be used if the primary route fails.C. Successor routes are flagged as active in the routing table.D. A successor route may be backed up by a feasible successor route.E. Successor routes are stored in the neighbor table following the discovery process. Answe
48、r: AD 134. Which of the following is true regarding the use of switches and hubs for network connectivity?A. Switches take less time to process frames than hubs take.B. Switches do not forward broadcasts.C. Hubs can filter frames.D. Using hubs can increase the amount of bandwidth available to hosts.
49、E. Switches increase the number of collision domains in the network. Answer: E135. Why has the network shown in the exhibit failed to converge?A. The no auto-summary command needs to be applied to the routers. B. The network numbers have not been properly configured on the routers.C. The subnet mask
50、s for the network numbers have not been properly configured.D. The autonomous system number has not been properly configured. E. The bandwidth values have not been properly configured on the serial interfaces.Answer: A136. DNS servers provide what service? A. Given an IP address, they determine the
51、name of the host that is sought.B. They convert domain names into IP addresses.C. They run a spell check on host names to ensure accurate routing.D. They map individual hosts to their specific IP addresses.Answer: B137. What are two characteristics of Telnet? (Choose two.)A. It sends data in clear t
52、ext format.B. It is no longer supported on Cisco network devices.C. It is more secure than SSH.D. It requires an enterprise license in order to be implemented.E. It requires that the destination device be configured to support Telnet connections. Answer: AE138. What TCP/IP stack configuration featur
53、es can DHCP provide, in addition to assigning an IP address? (Choose three.)A. default gateway B. DNS serversC. FTP server D. helper addressE. subnet maskF. TFTP serverAnswer: ABE139. Which of the following are key characteristics of PPP? (Choose three.)A. can be used over analog circuitsB. maps Lay
54、er 2 to Layer 3 addressC. encapsulates several routed protocolsD. supports IP only E. provides error correctionAnswer: ACE140. Refer to the exhibit. The network administrator has discovered that the VLAN configuration of SwitchC Is not synchronized with the rest of the switched network. Why is Switc
55、hC not receiving VTP updates?A. SwitchB is not relaying VTP advertisements to SwitchC.B. SwitchC has fewer existing VLANs than does SwitchA.C. SwitchA supports a greater number of VLANs than does SwitchC. D. SwitchC has a revision number higher than that being advertised.E. SwitchC should be operati
56、ng in VTP server mode to receive VTP updates.F. SwitchB should be operating in VTP server or client mode to relay VTP updates. Answer: D141. The network administrator of the Oregon router adds the following command to the router configuration: ip route 192.168.12.0 255.255.255.0 172.16.12.1. What ar
57、e the results of adding this command? (Choose two.)A. The command establishes a static route. B. The command invokes a dynamic routing protocol for 192.168.12.0. C. Traffic for network 192.168.12.0 is forwarded to 172.16.12.1.D. Traffic for all networks is forwarded to 172.16.12.1. E. This route is
58、automatically propagated throughout the entire network.F. Traffic for network 172.16.12.0 is forwarded to the 192.168.12.0 network.Answer: AC142. What will an Ethernet switch do if it receives a unicast frame with a destination MAC that is listed in the switch table?A. The switch will not forward un
59、icast frames.B. The switch will forward the frame to a specific port. C. The switch will return a copy of the frame out the source port.D. The switch will remove the destination MAC from the switch table. E. The switch will forward the frame to all ports except the port on which it was received.Answ
60、er: B143. A Cisco router that was providing Frame Relay connectivity at a remote site was replaced with a different vendors frame relay router. Connectivity is now down between the central and remote site. What is the most likely cause of the problem?A. mismatched LMI typesB. incorrect DLCIC. mismat
61、ched encapsulation typesD. incorrect IP address mappingAnswer: C144. The Ethernet networks connected to router R1 in the graphic have been summarized for router R2 as 192.1.144.0/20. Which of the following packet destination addresses will R2 forward to R1, according to this summary? (Choose two.)F. 192.1.1.144 Answer: AD 145. Which two practices help secure the configuration utilities on wireless access points from unauthorized access? (Choose two.)A. assigning a private IP address to the APB. changing the default
- 温馨提示:
1: 本站所有资源如无特殊说明,都需要本地电脑安装OFFICE2007和PDF阅读器。图纸软件为CAD,CAXA,PROE,UG,SolidWorks等.压缩文件请下载最新的WinRAR软件解压。
2: 本站的文档不包含任何第三方提供的附件图纸等,如果需要附件,请联系上传者。文件的所有权益归上传用户所有。
3.本站RAR压缩包中若带图纸,网页内容里面会有图纸预览,若没有图纸预览就没有图纸。
4. 未经权益所有人同意不得将文件中的内容挪作商业或盈利用途。
5. 装配图网仅提供信息存储空间,仅对用户上传内容的表现方式做保护处理,对用户上传分享的文档内容本身不做任何修改或编辑,并不能对任何下载内容负责。
6. 下载文件中如有侵权或不适当内容,请与我们联系,我们立即纠正。
7. 本站不保证下载资源的准确性、安全性和完整性, 同时也不承担用户因使用这些下载资源对自己和他人造成任何形式的伤害或损失。
